|
Humans are targets 36% of data breaches |
Humans make mistakes 90% of data breaches |
Compliance is essential Key standards like ISO 27001 |
Transform your employees into your first line of defence
Whether it's sharing passwords with colleagues, emailing sensitive data to the wrong recipient or falling victim to a phishing attack, employees are seen as the 'weakest link' in your cyber security.
That's why it's vital to understand where human vulnerabilities exist within your business and to train staff regularly to reduce the risk of data breach, fines or damage to your business's reputation.
Human Risk Management (HRM) is the new class of user-focused security that enables you to do just that through personalized security awareness training programs, periodic. phishing simulation campaigns, simplified policy management and ongoing dark web monitoring - completely managed for you.
Benefits-at-a-glance
- Drive user resilience to sophisticated phishing attacks
- Reduce user-related security incidents caused by human error
- Demonstrate compliance with key stands like ISO 27001 and GDPR
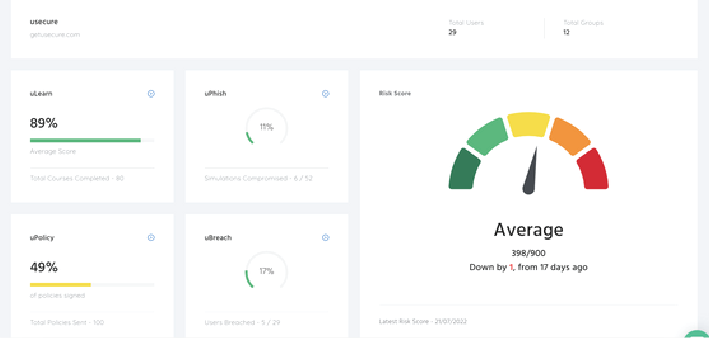
- Understand your business's employee security posture with a human risk score
- Dig deep into ongoing human risk with training, phishing and policy reporting
- Save time with readily-made courses, phishing campaigns and policy templates
- Simple setup, fast deployment and automated staff training reminders.
Key Features
Our HRM service offers a full-circle solution for assessing, reducing and monitoring human cyber risk, without hindering staff productivity.
Security Awareness Training
Assess each user's security knowledge gaps and automate regular training courses that tackle their unique risk areas.
- User-tailored training
- Automate reminders
- Cover essential topics
- Track user progress
Simulated Phishing
Automate periodic phishing simulations that assess your employees' ongoing risk to a range of attack techniques.
- Identify at-risk users
- Automate simulations
- Educate users on threats
- Instantly train at-risk users
Policy Management
Keep users well-versed on security processes with easy policy management and trackable eSignatures.
- Readily-made templates
- Automate reminders
- Track signatures
- All in one accessible place
How it works: Tailored. Measured. Effective.
Assess your employees' existing cyber risk areas through a quick 15-minute gap analysis assessment.
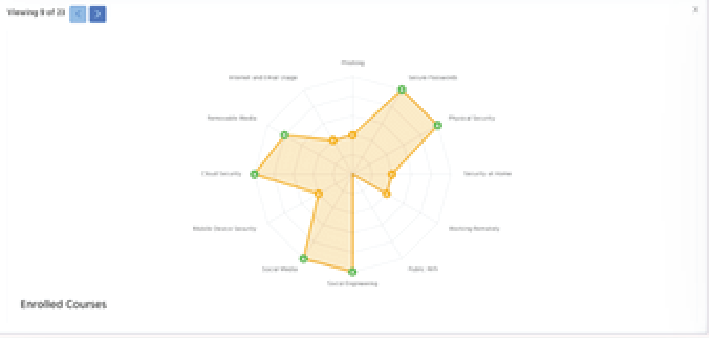
Strengthen user resilience with tailored training programs that prioritize courses to tackle each users' high-risk areas first.
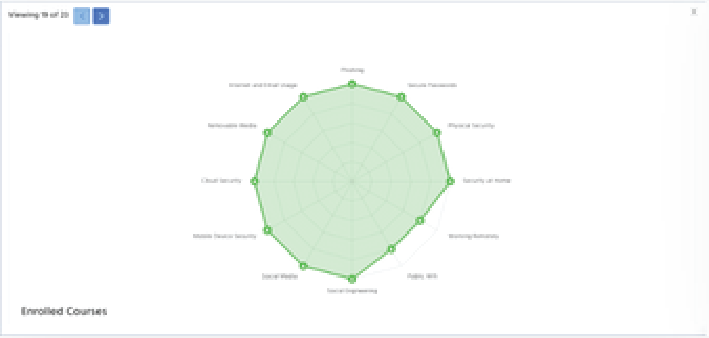
Understand ongoing human risk and measure the impact of the training through real-time reporting.
Showcase your human risk an data protection efforts in audits and demonstrate compliance standards.